Protecting the European Union from technological threats: The NIS2 directive
Rapidly evolving technologies have brought with them new cybersecurity challenges. Cyber-attacks, data theft and other threats can jeopardize not only individual privacy, but also national security. Against this backdrop, the European Union has adopted a series of directives designed to provide better protection against all these dangers.
The Network and Information Security (NIS) Directive was adopted in 2016 to strengthen the security of IT systems in the EU. It imposes security obligations on all operators of essential services such as energy, transport, healthcare, and banking, as well as digital service providers.
In France, these major players were required to report security incidents to the ANSSI, and to implement the security measures necessary to significantly reduce the exposure of their most critical systems to cyber risks.
Although the NIS Directive was a step forward for cybersecurity in Europe, rapidly evolving technologies have made it necessary to update the legislation. For this reason, the NIS Directive was revised in 2021 and became the NIS2 Directive in December 2022.
While building on the foundations of NIS1, the NIS2 directive greatly expands its scope of applicability as well as its objectives to compel organizations to better protect themselves on both a European and national scale.
In this article, we present the players affected by the new directive, the different areas covered and the processes to be considered to ensure compliance by October 2024.
Who is concerned?
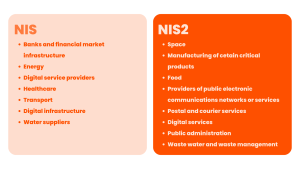
NIS2 extends the scope of the original directive, which was aimed at operators of essential services. The new directive now applies to providers of digital services, such as e-commerce platforms, search engines, social networks and cloud services. “On a national scale, NIS 2 will apply to thousands of entities belonging to more than eighteen sectors that will now be regulated. Around 600 different types of entity will be affected, including administrations of all sizes and companies ranging from SMEs to CAC40 groups” says Yves VERHOEVEN, Deputy Director Strategy at ANSSI.
This will apply to organizations operating in the business sectors listed in the table below, with more than 250 employees and annual sales of over €50 million and/or an annual balance sheet of over €43 million.
NIS2 also applies to any entity providing critical services within an EU member country, regardless of its location. In other words, any company based outside the EU could be subject even if it has no physical presence in the EU.
A tougher directive
The new directive introduces stricter incident reporting obligations, requiring critical entities to :
– Notify a significant security incident within 24 hours of its detection.
– Provide an initial assessment of the incident within 72 hours of detection.
– Submit a detailed final report within one month of incident detection.
NIS2 also provides for sanctions and remedies for essential service operators and digital service providers who fail to comply with security obligations: For essential entities, a fine of 10 million euros, or 2% of total worldwide sales. Penalties will be imposed by the competent national authority, in this case ANSSI in France.
In addition, the possibility for Member States to customize requirements in certain specific cases (which had led to considerable fragmentation in the implementation of NIS1) has been removed.
The three key areas of NIS2
To achieve these objectives, NIS2 focuses on three key areas: improving the cyber resilience of businesses in all relevant sectors, reducing inconsistencies in resilience between EU countries, and increasing the level of situational awareness and collective ability to prepare for and respond to cyber threats.
NIS2’s approach to improving corporate cyber resilience is based on extending the scope of the directive to the new sectors mentioned above. It also stipulates that all medium-sized and large entities operating in the sectors covered by NIS2 must comply with the proposed security rules, doing away with the distinction between OESs and digital DSPs, which are currently divided into three categories: online marketplaces, search engines and cloud service providers.
To reduce inconsistencies in resilience between EU countries, NIS2 provides for the alignment of security and incident reporting requirements, as well as oversight and enforcement provisions at national level. The aim is to ensure that all companies are required to manage cyber risks and report incidents to the relevant authorities.
Finally, NIS2 aims to improve the level of situational awareness and the collective ability to prepare for and respond to cyber threats. The directive provides for the establishment of a European crisis management framework, requiring Member States to adopt a plan and designate the competent national authorities responsible for participating in the response to cyber incidents and crises at EU level. The proposed directive also establishes an EU Cyber Crisis Management Liaison Network (EU-CyCLONe) to support the coordinated management of cyber incidents at EU level and ensure the regular exchange of information between member countries.
Preparing for the entry into force of the NIS2 directive
The repeal of the NIS directive and the transposition of the new directive will only be effective from October 18, 2024, leaving a planning margin of 21 months. However, it is essential that players affected by the NIS2 directive (especially if they are also affected by other recent European regulations) invest time and resources now to prepare for the change in their operational processes.
It is already essential for all these companies to evaluate and harmonize:
- Internal systems and information security policies
To protect oneself, it is essential to have an exhaustive view of both IT and operational systems in industrial environments, and to precisely define the impact of a process interruption. Defining an information security policy will help organizations to better protect the confidentiality, integrity and availability of data. The ANSSI has published a guide to developing information systems security policies, to help IS managers draw up an information systems security policy (ISSP) for their organization.
- Access Management
Organizations need to be able to identify and monitor access to their systems and data (all the more so when they open up external access to partners). Access security solutions such as CyberArk (leader in privileged account management) are recommended to reduce risks. Forbes found that 74% of data leaks involved the illicit use of a privileged account. Not to mention the many users who use passwords with a low level of security, or whose access remains even after they have left the company… The risk of this vulnerability being exploited by hackers has become even greater with the increase in teleworking and access to applications in the cloud. The implementation of a global identity management policy “enables the right people to access the right resources at the right time for the right reasons” (source Gartner).
CyberArk offers a guide to preparing for NIS2 with secure identities: Getting Ready for NIS2 – Why Identity Security is Key to Preparing for Compliance Updates (cyberark.com)
- Their incident management processes
Those affected by the NIS2 directive will need to have specific procedures in place to manage incidents and anomalies, to be able to quickly identify an incident, assess its level of criticality and impact, and deploy an action plan to restore the security of the systems concerned.
- How they report accidents
While NIS1 obliged OSEs and FSNs to report incidents with a significant impact rapidly, no specific timeframe was imposed. With NIS2, companies must organize themselves so as to be able to notify an incident within 24 hours of its detection, and must transmit detailed evidence within one month to the competent authorities (the ANSSI in France). This implies a high level of traceability and responsiveness. However, many organizations are not yet in a position to produce the required reports or track KPIs.
- Visibility of their company’s cyber risks
In a recent study, CLUSIF reported that 85% of its members were using performance indicators to manage their cyber strategy. However, only 36% have succeeded in automating their updating, and 43% in automating part of the data collection process, which is often carried out manually, using cumbersome Excel files. With Ignimission Platform, our customers are quickly relieved of these non-value-added tasks, and can easily collect the data they need to monitor their SSI indicators, then format them into shared dashboards.
Do you need to gain visibility over your ISS management? Simplify the collection and centralization of your security/compliance data with Ignimission Platform.
- Automatically collect multi-source data
- Manually enrich your data via forms
- Control the quality of your data
- Generate indicators and visualize SSI risk levels
- Easily collaborate and share your indicators
- Track security progress and control costs
Gain in efficiency, reliability and fluidity with Ignimission Platform: Request a demo!
Watch a video of our award-winning SSI portal solution at the CyberNight 2022 with Allianz and Opera Cyber!
Sources :
https://www.europarl.europa.eu/thinktank/fr/document/EPRS_BRI(2021)689333



